Member Article
Cambridge University sinks below Oxford in dark web cybersecurity analysis
Cambridge may well be the odds-on favourite to overturn Oxford’s recent dominance in the Boat Race this weekend, but research from dark web cybersecurity firm RepKnight shows that Oxford University is seemingly still pulling ahead of its rival when it comes to data protection.
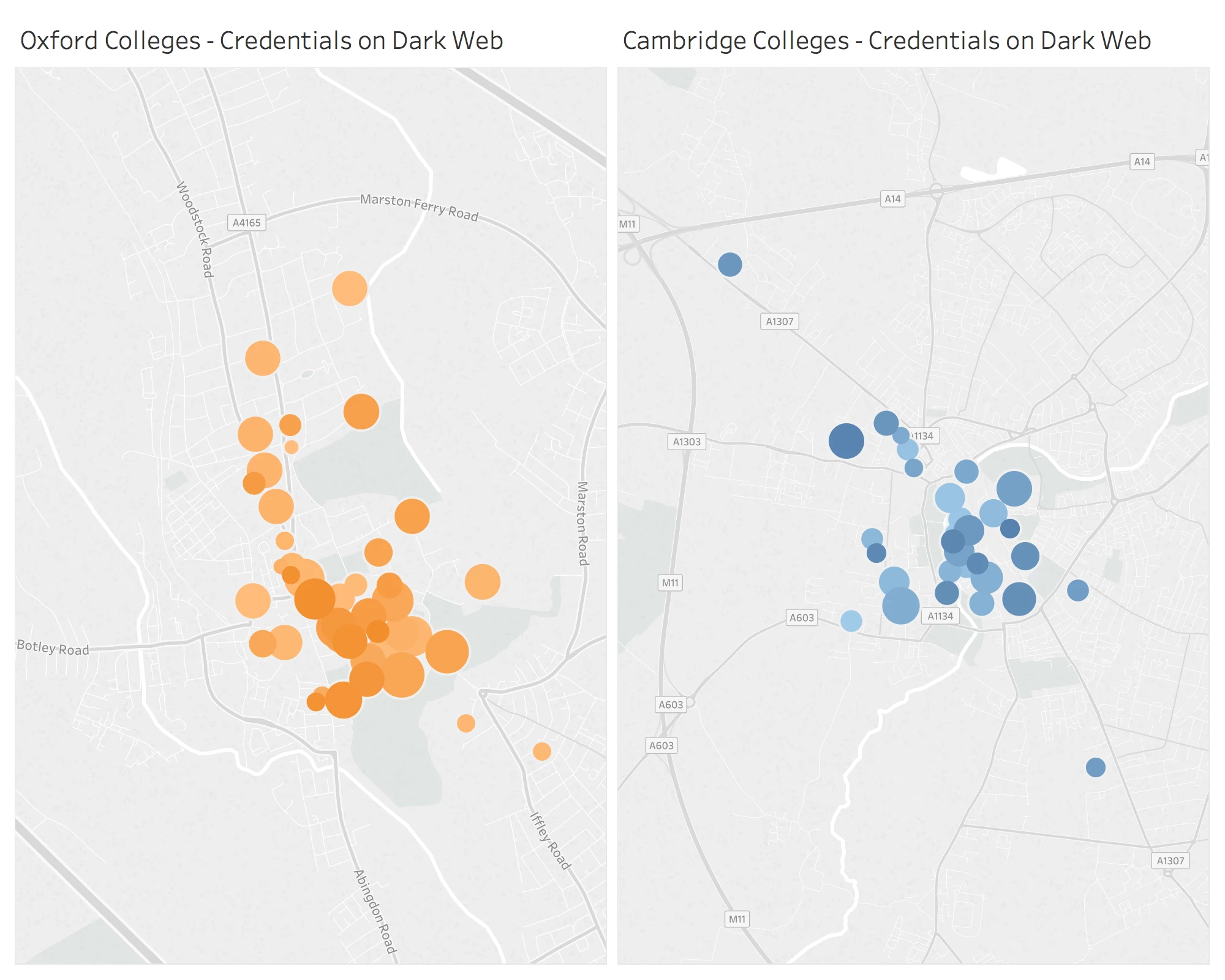
RepKnight found over 400,000 email addresses using the cam.ac.uk domain on the dark web – more than double the number that feature the ox.ac.uk domain* – as part of an ongoing campaign to raise awareness of the huge number of leaked and hacked credentials circulating on the dark web. These contact details are routinely used by cybercriminals to launch large scale phishing scams and, perhaps more significantly for the universities, can potentially be used to gain access to university computing resources and possibly commit data theft.
The analysis was done using RepKnight’s dark web monitoring tool BreachAlert, based on a comprehensive list of the domains for every Oxbridge college, faculty and administrative department. The exposed email domains were found across dark web, bin, dump and data breach sites, which feature more than 5 billion stolen, leaked or hacked credentials.
Interestingly, more than half of the Oxford University credentials identified were associated with the colleges, while the overwhelming majority (97%) of the exposed addresses from Cambridge were from faculties or university departments.
Educational institutions are an increasingly popular target for hackers and cybercriminals wanting to exploit their resources for activities such as cryptojacking – stealing high performance computer cycles to mine cryptocurrencies like Bitcoin. At the other end of the performance scale, universities may also have poorly secured legacy systems connected to the public internet, which can be accessed by hackers and used as proxies to carry out illegal activity. A wider analysis by RepKnight showed that the Russell Group of 24 leading UK universities have almost 5 million email credentials exposed on the dark web.
Patrick Martin, cybersecurity analyst at RepKnight, said: “It is often assumed that cybercriminals are primarily targeting commercial businesses. However, it’s not hard to see why the confidential data stored at universities might be a valuable commodity for criminals, given the links those institutions have to government agencies, supra-national organisations like the EU, and the private sector.
“Like most industries, universities are working hard to improve their cyber security capabilities. But the best network security often can’t defend against someone logging in using a stolen username and password. The vast majority of the credentials we see on the Dark Web are from third-party breaches, where an email address had been used on a site like LinkedIn or Dropbox, and that site was subsequently compromised – often including the user’s password. That’s why - in addition to securing their networks - every university should be deploying a dark web monitoring solution, to get a better understanding of their attack surfaces, and to get real-time alerts of leaks and breaches.”
This was posted in Bdaily's Members' News section by Patrick Martin .
Enjoy the read? Get Bdaily delivered.
Sign up to receive our popular morning London email for free.




 test article 123456789
test article 123456789
 hmcmh89cg45mh98-cg45hm89-
hmcmh89cg45mh98-cg45hm89-
 test456456456456456456
test456456456456456456
 test123123123123123123
test123123123123123123
 test xxxdiosphfjpodskhfiuodsh
test xxxdiosphfjpodskhfiuodsh
 Savour the flavour: North Tyneside Restaurant Week returns for 2024
Savour the flavour: North Tyneside Restaurant Week returns for 2024
 Six steps to finding the right buyer for your business
Six steps to finding the right buyer for your business
 Stephen signs off on a special night
Stephen signs off on a special night
 Life’s a Peachaus: Gillian Ridley Whittle
Life’s a Peachaus: Gillian Ridley Whittle
 Making a splash: Phil Groom
Making a splash: Phil Groom
 Making workplace wellbeing a priority
Making workplace wellbeing a priority
 A record of delivery, a promise of more: Ben Houchen
A record of delivery, a promise of more: Ben Houchen